Configuring IEEE 802.1x Authentication
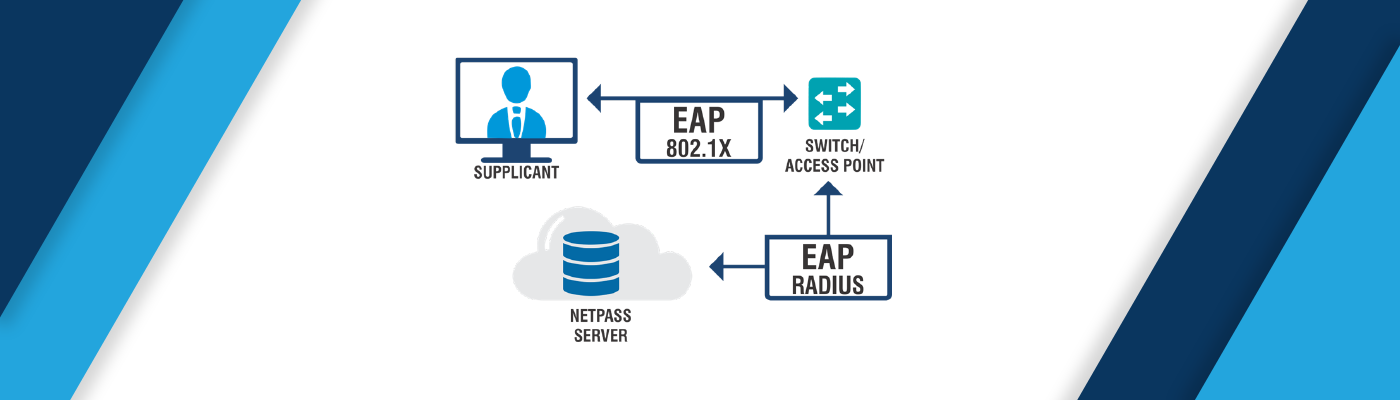
802.1x is an Institute of Electrical and Electronics Engineers (IEEE) standard which provides an authentication scheme to WLANs. A standard for Port-based Network Access Control (PNAC) is IEEE 802.1x. It is part of the 802.1 group of networking protocol and provides an authentication mechanism to devices wishing to get associated with a wired or wireless network. 802.1x defines then capsulation of Extensible Authentication Protocol (EAP) over IEEE 802 and also known as EAPOL (Extensible Authentication Protocol over LAN). It was later on modified as IEEE 802.1AE (MACSec) and 802.1AR (Secure Device Identity, DevID). 802.1x authentication uses three different parties, Supplicant, Authenticator, and Authentication Server. The supplicant provides information like Username / Password or Digital Certificate to Authenticator and Authenticator forwards request to Authentication Server for Access Grant or Reject. EAPOL operates at the network layer which resides on the top of the data link layer.
IEEE 802.1X controls access to wireless or virtual local area networks (VLAN) and applies traffic policies based on user identity and credentials. IEEE 802.1X ensures a user authentication framework where network access is denied upon failed authentication. Built for wired networks, IEEE 802.1X requires very little processing power and is well-suited to wireless LAN applications. IEEE 802.1X supports multiple authentication methods, such as token cards, public key authentication and certificates. Extensible Authentication Protocol (EAP) simplifies interoperability and compatibility through EAP over the local area network. The authentication protocols that operate inside the IEEE 802.1x and are suitable for wireless networks include EAP-Transport Layer Security (EAP-TLS), EAP-Tunneled TLS (EAP-TTLS), Protected EAP (PEAP). These protocols permit the network to authenticate the client while also permitting the client to authenticate the network.
So, basically 802.1X is used for WPA-Enterprise in wireless networking. Instead of pre-shared keys, it is used in wireless networking so that there can be per-user authentication and it also uses a different WPA master key for each wireless user which enhances the security.
802.1x uses three terms that one should likely know:
Supplicant:
It is the user or client device that wants to be authenticated and granted access to the network.Authentication server:
It is the actual server performing the authentication, most commonly a RADIUS server.Authenticator:
This is the device between the Authentication Server and Supplicant.Why 802.1x Authentication Is Important?
As networks shifted to Wi-Fi, IT management infrastructure picked up and moved to the cloud. An opportunity to simplify the delivery of better network security emerged. Innovations made it possible for IT administrators to replicate just about everything to do with 802.1x implementations up into the cloud. Certainly, this led to no more on-prem RADIUS servers and IdPs like Active Directory to constantly maintain or to make sure that each endpoint had the correct supplicant.
Today, in most of the verticals a network infrastructure needs Security and flexibility exclusively as both are equally important. Security is crucial on any network while flexibility for users needs to allow the ability to roam. To carry out the requirements, it needs highly secure device authentication method. It also needs the appropriate network access for users that needs to be determined from their authentication credentials in addition. LAN to LAN security is of much importance now with BYOD as compared to WAN to LAN. 802.1x user authentication solves these all requirements. 802.1x is a security protocol that works with 802.11 wireless networks such as 802.11b, g, n, as well as with wired devices. The purpose of 802.1x is to accept or reject users who want access to a network using RADIUS authentication before they are able to transmit packets/frames to the network.
802.1X offers unprecedented visibility and security as well as identity-based access control at the network edge. You can meet the needs of your security policy with favorable design and well-chosen components while minimizing the impact on your infrastructure and end-users.
The need for secure network access in recent times is at high demand. Guests, consultants, and contractors these days require access to network resources over the same LAN connections as usual employees who can probably bring unorganized devices into the workplace themselves. The possibility that unauthorized people or devices will gain access to controlled or confidential information has increased as data networks become increasingly indispensable in day-to-day business operations. Leveraging the intelligence of the network at the access edge will lead to the best and most secure solution to vulnerability.