WPA2 Enterprise Authentication: WPA2 PSK
WPA2 is the most recent security protocol developed by the Wi-Fi Alliance. It stands for Wi-Fi Protected Access 2. Wi-Fi Protected Access 2 is a network security technology generally used on Wi-Fi networks.WPA2 is an advancement of the WPA Network Protocol. The chief difference between WPA2 and WPA is that the former further improves the security of a network as it requires using an even more powerful encryption method called the AES.
WPA2 Enterprise makes use of IEEE 802.1x, which offers enterprise-grade authentication. WPA2-Enterprise has been around since 2004 and is still a gold standard for wireless network security by delivering over-the-air encryption and top-level security. WPA2 makes use of CCMP (Counter Cipher Mode with Block-Chaining Message Authentication Code Protocol) and AES (Advanced Encryption Standard) algorithms in order to provide more security to the business enterprises.
WPA Enterprise authentication is usually required in corporate or government environments. WPA2 Enterprise usually verifies network users through a RADIUS server or it may also use other authentication servers. WPA2 makes use of 128-bit encryption keys and dynamic session keys to guarantee the privacy of wireless networks as well as enterprise security. An authentication type is chosen to match the authentication protocol of the 802.1X server. Corporate or government environments mostly use Enterprise Mode. WPA2 implements the full IEEE 802.11i standard.
WPA2- Personal uses pre-shared keys (PSK)
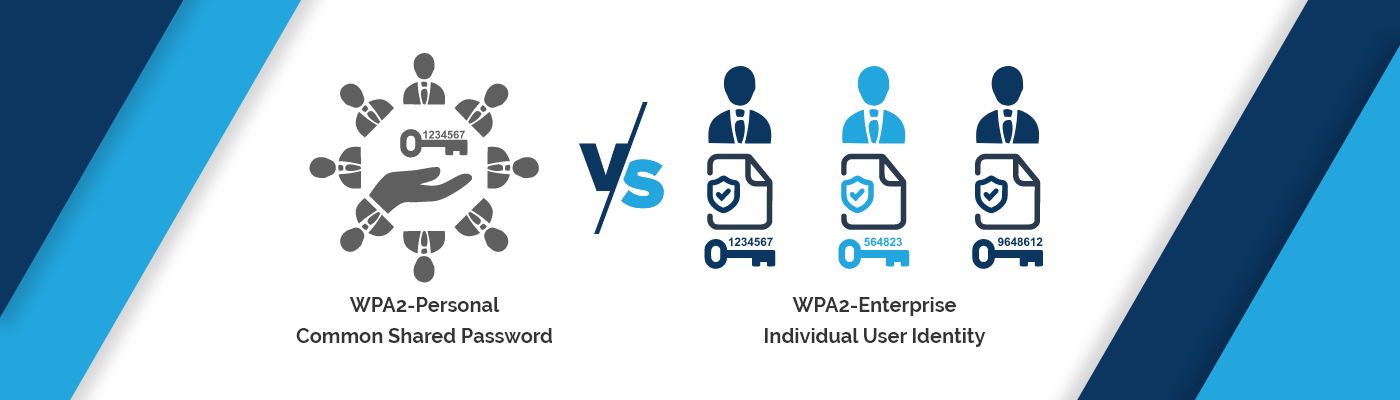
WPA2-Personal or WPA2 Pre-Shared Key (WPA2-PSK) is a widely adopted method to secure wireless networks. A pre-shared key or passphrase is used for authentication, in the Personal mode. In a WPA2-PSK that is wpa2-personal, access is granted by common pre-shared key means a common password at the router level and it does not require an additional authentication server. Today, most of the enterprise and home segments are using this method. Anybody who knows the password can join the network by using it.
WPA2-PSK (Pre-Shared Key) requires a single password to get in hold with the wireless network. It’s commonly a notion that a single password to access Wi-Fi is safe, but it’s only as much as one trusts the individual using it. Basically WPA2-PSK is a technique of securing a network using WPA2 with the use of the optional Pre-Shared Key (PSK) authentication. It is mostly designed for home users without an enterprise authentication server.
To encrypt a network with WPA2-PSK the router is not provided with an encryption key but rather a plain-English passphrase between certain amounts of characters. The passphrase along with the network SSID by using a technology called TKIP (for Temporal Key Integrity Protocol) is used to generate unique encryption keys for each wireless client. Encryption keys are constantly changed.
WPA2 Enterprise is especially designed for organizations
By using WPA2-Enterprise all the security gaps can be filled i.e.1x authentication for the user device. In this each user has a unique credential (Username and password or digital certificate or both) to connect to the wireless network; we can also use x.509 digital certificates for user device authentication. This method uses a RADIUS server for authentication. We can set up this authentication in the SMB and the enterprise organization for better security for network. A digital certificate can be issued self-signed or can be managed by PKI- public key infrastructure i.e Digicert (public CA).
Organizations that require a government-grade wireless network security should use Wi-Fi Protected Access 2 Enterprise (WPA2-Enterprise). To better the flexibility of critical networks, WPA2-Enterprise was lately enhanced with Protected Management Frames, which further secure WPA2 against packet forging and eavesdropping. All Wi-Fi Certified devices support WPA2 for additional protection.
Deploying WPA2-Enterprise
In order to deploy WPA2-Enterprise, it requires a RADIUS server that handles the task of authenticating a user’s network access. The actual authentication process is based on the 802.1X policy and comes in several different systems labeled EAP. As each device is authenticated before it gets connected, a personal encrypted tunnel is effectively created between the device and the network.
EAP (Extensible Authentication Protocol) Extensions under WPA and WPA2 Enterprise
The choice of EAP depends on the level of security you need and your server/client specifications. There are more than ten types of EAP but these three are the most popular ones.
- PEAP (Protected EAP): In this protocol users are authenticated through the usernames and passwords they enter while connecting to the network. The easiest EAP type to implement is PEAP.
- TLS (Transport Layer Security): This type requires more time to implement and maintain. It is very secure because of both server and client validation is done with SSL (secure socket layer) certificates. Rather than connecting to the network with usernames and passwords, end-user devices or computers must have an SSL certificate file.
- TTLS (Tunneled TLS): This version of TLS doesn't require security certificates and reduces network management time. TTLS does not have a native support in Microsoft Windows, hence, it requires a third-party client.