Identity Management - In Enterprises
Generally, the term, Identity management (IdM) means the task of controlling information about users on computers or such devices. This constitutes the information that authenticates the identity of a user and the information that describes information and actions they are authorized to access and/or perform.
Identity management is a framework of policies or actions and technologies for making sure that legitimate people in an enterprise have proper access to network. Identity management is also referred to as identity and access management. IdM systems fall under the umbrella of IT security.
In simple words - Identity management (ID management) is the organizational procedure for identifying, authenticating and authorizing an individual or group of human beings to have or gain access to applications, systems or networks by blending user rights and restrictions with chartered identities.
Identity management is a prominent part of the enterprise security plan, as it is responsible for both the security and productivity of the organization. In a lot of organizations, users are granted more access privileges than they actually require with respect to performing their functions. Attackers can take undue advantage of compromised user credentials to gain access to organizations' data and networks. By using identity management, organizations can secure their corporate assets against many threats. Identity management systems can add an additional layer of protection by ensuring that user access policies and rules are applied from time to time across an organization.
To help organizations add identity and access management functionality to their applications, protect user accounts, and scale with confidence, a customer identity, and access management (CIAM) platform called Identity Service Platform is deployed. Authentication and access policy for the user on the network are the main elements of identity and access management. The IAM software is equipped with features that allow the user to ease all procedures related to these processes. Such features include:
- Automatic provisioning of user accounts
- Workflow and self-service management
- Password management
- Single Sign-On (SSO)
- Audit and Compliance
Identity and access management (IDM) are useful in many ways: it ensures regulatory compliance, enables cost savings, and simplifies the lives of customers by enhancing their experience. The importance of IAM is clear with regard to recent surveys and research. User information, whether it is passwords or email addresses, can quickly become a difficult task to track without an appropriate control system in place. IAM helps protect against security breaches by allowing administrators to automate a number of user account related tasks. An IAM system can also help in tracking many of the auditable items required by industry policies and standards, such as access control implementation and monitoring.
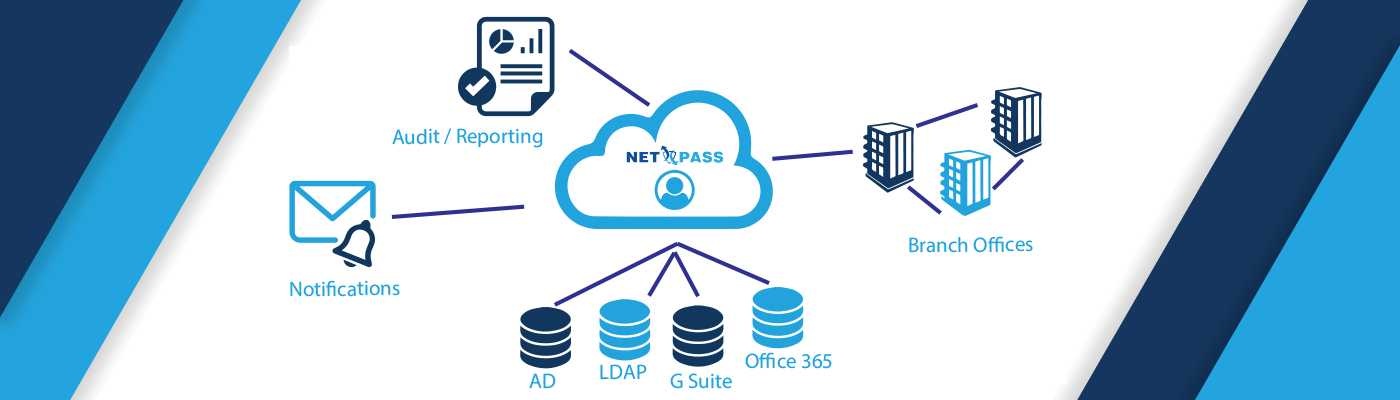
NETPASS can create multiple directory on single centralized database on RADIUS for all branch offices.
NETPASS helps to implement centralized identity management by creating a centralized user database and directory; NETPASS can also define multiple user groups and define different policies for individual groups.
RADIUS
Remote Authentication Dial-In User Service (RADIUS) is employed mostly for network services, such as wireless connections, network infrastructure. RADIUS is mostly preferable for applications requiring general authorization. It is now highly consumed by organizations to control wireless Access. It is traditionally known as Authentication, Authorization, and Accounting or AAA.
LDAP
The Lightweight Directory Access Protocol (LDAP) is an open-source protocol that is not associated with any specific vendor. It certainly provides the basis for Microsoft’s Active Directory. LDAP is one of the oldest and most promising identities and access management protocols was established as an industry-standard in the 1990s. As the name suggests, LDAP is connected with directory access.
Active Directory (AD)
AD is developed by Microsoft and is used as a user-identity directory service for Windows domain networks. Though proprietary, AD is a part of the Windows Server operating system and is thus widely deployed.
Since NETPASS supports RADIUS, LDAP and AD setups, according to these cases, if a customer is using LDAP or AD –NETPASS can sync that data to RADIUS. Hence it will integrate with LDAP and AD in the back end and make RADIUS the basis for it. It can also be integrated with an external directory like G Suite and Office 365. Accordingly, users can use the same user name set already in G Suite or in Office 365, for the 802.1x authentication. NETPASS provides out of the box integration with Office 365 in order to embed access control and monitoring policies that are consistently applied by the Cloud provider no matter where the user accesses it from.
It is clear that there are a variety of authentication protocols on the market. Each of the identity and access management standard has different applications. It is very important to choose a solution according to the needs of your organization. NETPASS works with organizations and institutions to implement appropriate protocols to ensure data security. NETPASS specializes in helping organizations create identity and access management solutions that best suit their unique needs. Streamlining identity and access management functions will not only save time, but it also improves security and compliance by eliminating manual errors and providing comprehensive documentation and reporting tools.