X.509 Authentication - Digital Certificate-Based Authentication
Data security is one of the most necessary aspects of every modern data platform. The process of verifying that a user is who they say they are is “Authentication”.
A digital certificate is a digital document that includes the public key related to an individual, organization, or a computer. Certificates are issued by CA - certificate authorities. They have documented policies for determining owner identity and distributing certificates.X.509 digital certificate-based authentication is a standard-based security framework that is used to secure private information and transaction processing. Certificates are exchanged in a way to ensure that the one who presents a certificate possesses the private key associated with the public-key which is contained in the certificate.
Certificate-based authentication allows users to safely access a server by exchanging a digital certificate rather than a username and password. Certificate-based authentication is built by using to the maximum advantage of the X.509 public key infrastructure - PKI standard. By mutually authenticating both the client, using a trusted party (the Certificate Authority (CA)) and the server during the TLS handshake the Certificate-based authentication offers stronger security. It is only possible to connect to the real server because the certificate is signed, and centrally manage the certificates using the CA for rotation or revocation. MongoDB supports X.509 certificate authentication for it’s the usage with a secure TLS/SSL connection.
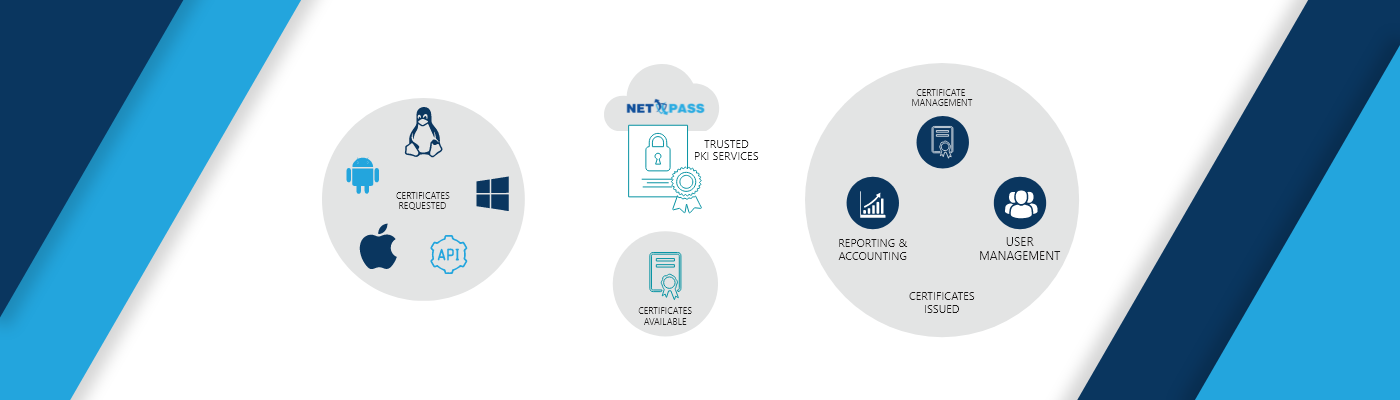
An X.509 certificate is a digital certificate that uses the globally accepted international X.509 public key infrastructure (PKI) standard to verify that a specific public key belongs to the user, service identity or computer contained within the certificate. The format of the public key certificate is defined by the X.509 standard. X.509 certificates are utilized in many Internet protocols, for instance, TLS/SSL, which is the basis for HTTPS that is certainly a secure protocol for browsing the web. Offline applications, like electronic signatures, also use X.509 certificates.NETPASS can issue an X.509 certificate for computing and IoT devices. Some IoT devices allow installing the certificates, as these devices support certificate-based authentication for the security.
NETPASS can generate separate X.509 certificates for each user device and can also bind with user devices.
With an additional cost, NETPASS can integrate with DigiCert as well as publicly signed a CA certificate from external PKI service provider – DigiCert.
A certificate-based authentication uses public-key cryptography or self-sign on the digital certificate to authenticate a user. The server then confirms the validity of the digital signature and if the certificate has been issued by a trusted certificate authority or not.
Configuring X.509 Certificate Authentication for clients:
All SDK clients support the X.509 certificate-based authentication feature. However, the recent versions support it, so keep a check on the release notes for your SDK versions.
SSL/TLS relies on the X.509 certificate and it is the official standard for public key certificates and. In the client, you must use an authentic or valid X.509 certificate that is generated and signed by the same root certificate authority (CA) as the server.Since the early TLS days, most of the common web browsers have been supporting client-authentication. One can configure the client certificate in their browser certificate store and then they are good to go!
An X.509 certificate contains the following information:
- Version: It demonstrates which X.509 version applies to the certificate. (This indicates what data the certificate must include)
- Serial number: While creating the certificate, the identity creating it must assign a serial number that differentiates it from other certificates.
- Algorithm information: This is the algorithm used by the issuer to sign the digital certificate.
- Issuer’s unique name: The name of the entity issuing the certificate. (usually a certificate authority)
Applications of the X.509 Certificate:
A browser alerts the security of a webpage in a few different ways. When a browser gives this information it ultimately comes from reading the X.509 certificate of a page and verifying the security or safety of the page through TLS/SSL certificates. An SSL, or “Secure Sockets Layer,” is a type of technology that protects personal data from getting stolen from a web page. An advanced version of SSL is TLS or “Transport Layer Security”. TLS/SSL certificates are made possible by a pre-existing X.509 certificate that secures the site itself. The letters ‘HTTPS’ at the start of a link is an indication to users that the site utilizes a TLS/SSL certificate and is secured by an X.509 certificate. Hence most websites purchase a certificate to protect sensitive customer input, for example, credit card information. X.509 certificates are also used to create digital signatures that verify the identity of specific users and certificate authorities online.